In 2022, more than 34,000 incidents of cyber-accidents were reported in Switzerland, a large number of them due to phishing. And that’s not including all the unreported cases. What can you do to protect your organisation from cyber risks? How can you protect your collaborators’ email, which is often the target of cyber-attacks? Eskills proposes Cybercafés, 10-minute capsules to raise your teams’ awareness of cyber risks and good practice in cybersecurity and data protection.

Online, phishing (not fishing) is an underhand technique used by cybercriminals to trick users into revealing sensitive information. It is a scam that attacks the computer system via an e-mail. How does it work? By posing as trusted entities, such as partners, suppliers of software used in the company, the bank or colleagues, through e-mails or electronic messages (SMS, messenger, chat, etc.).
Imagine receiving an email informing you that you’ve won a considerable sum of money or that the software you use every day at work needs to be updated urgently, otherwise you’ll be blocked from accessing it and you’ll lose your data. Sound familiar? That’s how phishing starts its subtle game. With phishing emails, hackers seek to deceive their victims’ vigilance by playing on their emotions. And anyone can be fooled by a deceptive sender. All it takes is one click, and often, even if you abandon the procedure in midstream, it’s already too late.
Often, the action requested of the recipient in this type of message may seem harmless, which makes Internet users less suspicious. For example, these messages ask the recipient to log in to their account using their password, to visit a website, to register their telephone number, to update a payment method, to change information, and so on. It is not always a question of making a payment on the Internet, which can trick Internet users into being more vigilant.
If an employee inadvertently clicks on a link contained in a fraudulent email, there is a risk not only of their workstation and data being compromised, but also of all the company’s sensitive data being compromised. All it takes is for one person to perform the action requested in the email for cybercriminals to use it as a gateway to access and steal confidential data. The classic scenario is a ransom demand in exchange for the return of the data. Of course, even if a ransom is sent, it is rare to recover one’s data. Cyber attacks are constantly evolving, becoming more sophisticated and harder to identify. By investing in awareness-raising, you give your teams the means to fight cyber threats and malicious acts effectively.

The best defence against phishing is to acquire the knowledge that will enable everyone to adopt the right reflexes to ensure that everyone is safe when faced with this type of email. The first measure is to step back and take the time to analyse the suspect email.
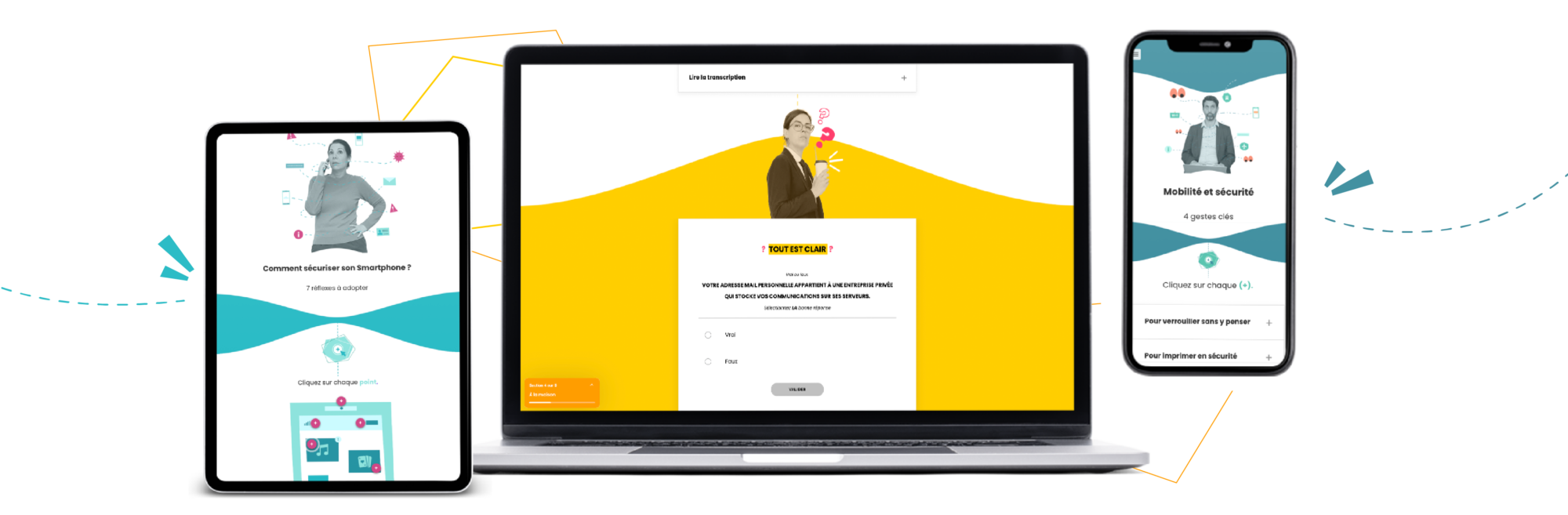
With this in mind, we have created the Cybercafés, a series of 10-minute capsules on different themes designed to raise your employees’ awareness of good practice in cybersecurity and data protection. These capsules are punctuated by a humorous web series, featuring everyday situations, quizzes and fun media to help you integrate this new knowledge easily and sustainably.
In each capsule, users are put in a real-life situation in which it is easy for them to recognise themselves and understand how to use what they have learned to distinguish between genuine and falsified emails.
Adresse
23, rue des Eaux-Vives –
1207 Genève – Suisse
Téléphone
+41 22 700 12 01
Made with ❤️ in Switzerland🇨🇭
2023 © by eSkills • All rights reserved